Cyber Security Melbourne
Essential 8 Matuirity model.
Protection Against Cyber Threats
Home » IT Security » Cyber Security
Melbourne's Leading Digital Security Specialists
Given how integral the internet is to daily operations, cyber security has become one of the most important components of running any business.
Keeping your business network secure is of the utmost importance, and you want to engage with a cyber and IT security provider that can keep you on top of potential threats to your operations and data privacy.
Read on to learn how Setup4 can cover your cyber security needs and keep your business safe from online threats.
At Setup4, we specialise in protecting businesses from the many IT and cyber security threats that present themselves.
We offer onsite IT support in Melbourne and remote IT support throughout Australia. Your entire network can be secured through endpoint protection and live threat responses.
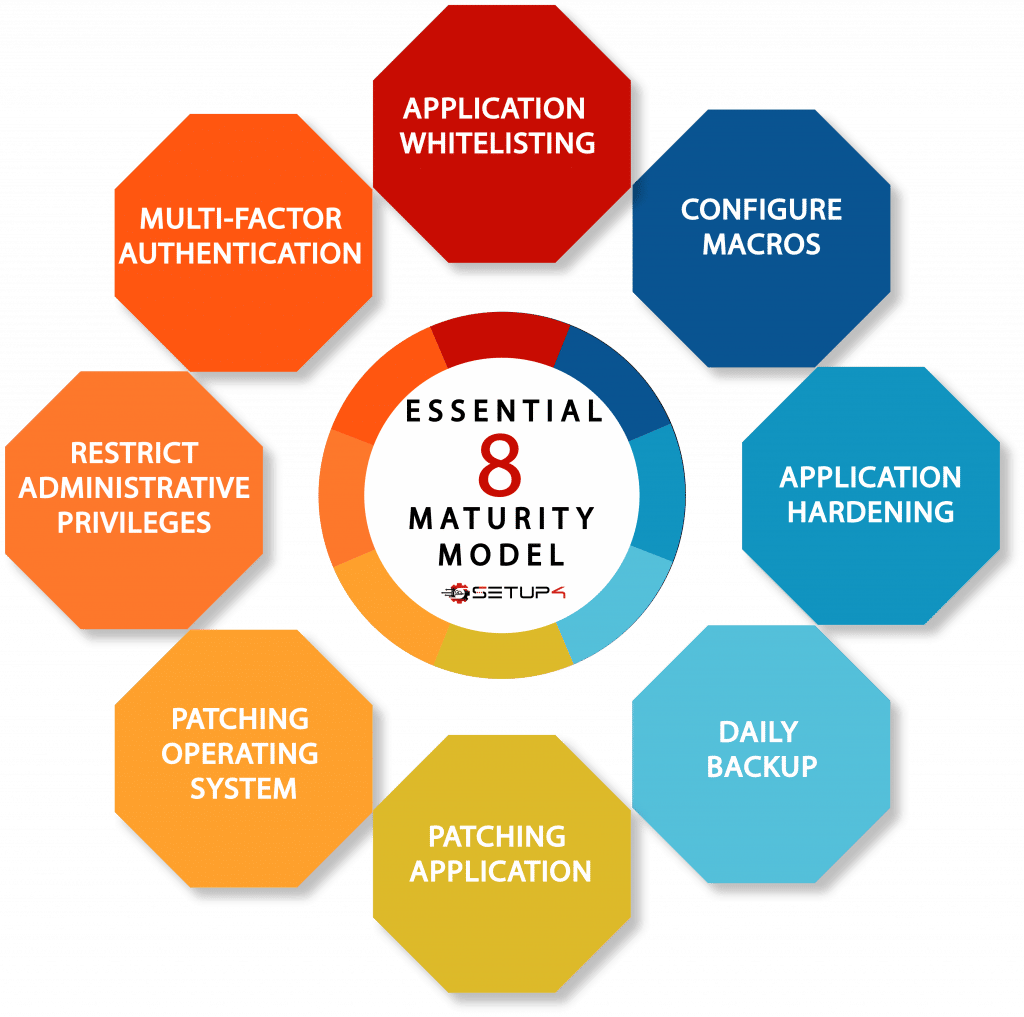
Cyber Security Essential Eight Maturity Model
The Essential Eight are designed to protect Microsoft Windows-based internet-connected networks.
While the Essential Eight may be applied to cloud services and enterprise mobility, or other operating systems, it was not primarily designed for such purposes and alternative mitigation strategies may be more appropriate to mitigate unique cyber threats to these environments.
In such cases, organisations should consider alternative guidance provided by the ACSC.
Talks to one of our consultants who can help you on your cyber security Journey.
Cyber Security and Privacy Assessment
We provide initial cyber security and privacy assessments for your business to give you an overview of what you’re doing right and what needs to be addressed to better your IT security.
Privacy is of critical importance for any business, and doubly so if you handle sensitive customer data. After an initial assessment, a deeper audit can be offered for your cyber security setup.

Cyber Security Auditing
After an initial assessment, we’ll provide a comprehensive audit to identify the key cyber security threats that your business may be facing. This cyber security audit is done in four steps:
- Define the threats: First, we scan and list all the threats that could affect your endpoints, email server, cloud server, local IT infrastructure, data and your customers.
- Evaluate your security: We assess your company’s ability to defend against all cyber threats by putting your IT systems through a series of tests.
- Likelihood of threats: Setup4 takes your list of threats and scores them on a scale of 1–10 based on how likely they’ll occur and the threat they’d present to your business’s IT infrastructure.
- Design a defence strategy: In the final step, we develop a strategy to address the most probable threats you may face. Security solutions vary for each threat, and our consultants will make the appropriate recommendations to protect your business from costly breaches.
Computer and Server Security
Setup4 offers extensive endpoint protection, which is designed to focus on a business’s physical network devices. These include computers and laptops, printers and scanners, smart devices, servers, etc. — any device that functions to exchange valuable data online through an IT network.
Our IT cyber security experts at Setup4 are always on the lookout for threats such as viruses, data hacks, and more. We keep these external threats away from your business network so no one can access valuable data through an endpoint without explicit permission.


Ransomware Protection
Ransomware protection is a multi-faceted approach that utilises different tools, education, and contingency plans.
These protections can include the following:
- Robust antivirus and antimalware programs;
- Strong email filtering that accounts for spam and phishing scams;
- Web browser protection that blocks questionable, non-secure, and malicious websites;
- Strong firewall protection that can include the use of an enterprise-level firewall;
- Daily data backups that lessen the impact of potential ransomware attacks;
- Updated passwords and comprehensive two-factor authentication;
- Security awareness training that educates employees on safe web browsing and how to identify online threats;
- Detailed action plans to follow in the event of a data breach; and
- Network segmentation that makes it harder for cybercriminals to gain access to the entirety of your business’s network data
Internet Cyber Security
Ensuring you and your employees’ internet security is accounted for is of critical importance. Similar to how antivirus and antimalware software can help protect you from ransomware, they also make online browsing safer.
Internet security is also bolstered by having enterprise-level firewalls in place and secured servers. Blocking out questionable websites and identifying those that have security issues or have likely been compromised with malicious software or code makes the internet safer to navigate.
Education is also key – ensuring all staff are aware of best practices and how to identify potential threats or phishing scams.

What Is Included In Our Cyber Security Service
Application control is implemented on workstations and servers to restrict the execution of executables, software libraries, scripts, installers, compiled HTML, HTML applications, control panel applets and drivers to an organisation-approved set.
Application Control
Patch Application
Patches, updates or vendor mitigations for security vulnerabilities in internet-facing services are applied within two weeks of release, or within 48 hours if an exploit exists. Patches, updates or vendor mitigations for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products are applied within two weeks of release, or within 48 hours if an exploit exists
Microsoft Office macros are disabled for users that do not have a demonstrated business requirement. Only Microsoft Office macros running from within a sandboxed environment, a Trusted Location or that are digitally signed by a trusted publisher are allowed to execute. Only privileged users responsible for validating that Microsoft Office macros are free of malicious code can write to and modify content within Trusted Locations
Configure Office Macros
User Application Hardening
Web browsers do not process Java from the internet. Web browsers do not process web advertisements from the internet. Internet Explorer 11 is disabled or removed. Microsoft Office is blocked from creating child processes. Microsoft Office is blocked from creating executable content. Microsoft Office is blocked from injecting code into other processes.
Requests for privileged access to systems and applications are validated when first requested. Privileged access to systems and applications is automatically disabled after 12 months unless revalidated. Privileged access to systems and applications is automatically disabled after 45 days of inactivity.
Restrict Admin Privileges
Patch Operating Systems
Patches, updates or vendor mitigations for security vulnerabilities in operating systems of internet-facing services are applied within two weeks of release, or within 48 hours if an exploit exists. Patches, updates or vendor mitigations for security vulnerabilities in operating systems of workstations, servers and network devices are applied within two weeks of release, or within 48 hours if an exploit exists.
Multi-factor authentication is used by an organisation's users if they authenticate to their organisation’s internet-facing services. Multi-factor authentication is used by an organisation’s users if they authenticate to third-party internet-facing services that process, store or communicate their organisation's sensitive data. Multi-factor authentication (where available) is used by an organisation’s users if they authenticate to third-party internet-facing services that process, store or communicate their organisation's non-sensitive data.
Multi-Factor Authentication
Daily Backups
Backups of important data, software and configuration settings are performed and retained in a coordinated and resilient manner in accordance with business continuity requirements. Restoration of systems, software and important data from backups is tested in a coordinated manner as part of disaster recovery exercises. Unprivileged accounts, and privileged accounts (excluding backup administrators), cannot access backups.
Why Choose Setup4 for Cyber and Digital Security?
Setup4 offers a comprehensive solution for all your IT needs, with onsite and remote IT support and securing your networks and devices from all manner of cyber security and digital threats.
We focus on building strong relationships with our clients and provide 24-hour support so we’re always there when you need us. Stay focused on running and growing your business, knowing that all your IT and cyber security needs are taken care of.
Learn more about us or get in touch to manage your cyber security today.
Endpoint Cyber Security FAQs
What is endpoint cyber security?
Endpoint cyber security is the process of protecting endpoints from external cyber attacks such as phishing, ransomware and data hacks. These endpoints are physical devices that connect to a computer network and share information with each other. For example: mobile devices, desktop computers, embedded devices, and servers that connect to your business’s IT network. As they are vital for the exchange and processing of valuable data, these endpoints need to be protected.
Endpoint security is just one part of the ACSC strategies to mitigate cyber security incidents and protect your business from external threats.
What are Strategies to Mitigate Cyber Security Incidents by Australian Cyber Security Centre (ACSC)?
The purpose of the ACSC is to provide up-to-date and nationwide cybersecurity principles that will affect every Australian business with an IT network.
These cyber security principles work in tandem with our values at Setup4 and are grouped into four key activities that follow:
Govern
Identifying and managing security risks.
Protect
Implementing controls to reduce security risks.
Detect
Detecting and monitoring cyber security risks that could be potentially harmful.
Respond
Responding to and recovering from cyber security incidents.
What is the Essential Eight Maturity Model?
The essential eight maturity model is designed to protect Microsoft Windows-based IT networks. This model can be applied to cloud services, enterprise and Ecommerce-based operating systems. But it will not be as efficient as Windows-based software such as Microsoft 365, Microsoft Teams, OneDrive and others.
We go through the following steps to complete the model:
- Application Control
- Patch Application
- Configure Microsoft Office Macros
- User Application Hardening
- Restrict Admin Privileges
- Patch Operating Systems
- Multi-Factor Authentication
- Daily Backups
Why should I sign up for endpoint cyber security?
In recent years, there has been a systematic increase in the number of nationwide cyber attacks in Australia and a greater need for a robust, dynamic and active cyber security setup.
As a business that deals with data, whether that is as a SaaS or by hosting clients’ private information, it is a legal requirement to ensure that the best data security practices are being used as issued by the ACSC. Our team of IT security professionals ensure that your client’s and customer data is protected.
What is the difference between endpoint cyber security vs network cyber security?
Endpoint security is specific to safeguarding the devices that manage and exchange key data across your business’s IT network. These devices include laptops, phones, tablets and services and can be used as access points by cyber-attacks if they are not kept adequately secure.
Network security relates to the protection of the internal network infrastructure itself. Any data that is sent across the network needs to be able to defend against threats that aim at cloud data, firewalls and networked devices.
Both types of security are vital for the IT management and running processes of a business.
Our Latest Cyber Security Articles
Have a Project in mind?
Let's have a chat with our Experts.
Need to talk to an IT Expert? Fill out the form and one of our experts will get in touch with you very shortly.
If you prefer to give us a call, we are ready to talk to you.
We are Easy to Reach
What You Get
- We Phone and Email You
- Cost Estimate of your project
- In-Person Visit





